Acer Update Decrypter Executive Order
Update May 21: Microsoft has stopped selling the Huawei MateBook X Pro on the company's online store, as spotted. It's not clear why the product was removed, and Microsoft has not provided comment on the matter.When Huawei entered the laptop market in 2017, nobody expected the company to rise as quickly as it did. The remains one of our favorite Windows 10 notebooks, and one of the we'd ever reviewed.Now, less than two years after its release, the fate of hangs in the balance as escalating tensions with the U.S. Government threaten to cripple the company's international operations.Huawei has seen its reputation plummet in the U.S. In the past few years after the U.S. Accused the company of committing corporate espionage for the Chinese government, then from using Huawei equipment. Most recently, Huawei was placed on an export blacklist by the U.S.
Department of Commerce and President Donald Trump signed an executive order stating that American companies supplied by companies that the government deems a threat to national security.Not long after the latest restrictions, and semiconductor companies Intel, Qualcomm, Xilinx and Broadcom announced that they would stop supplying the Chinese company until further notice. That means Huawei can no longer purchase parts unless it receives permission from the U.S. Microsoft official academic course series pdf editor. Government, a rule that could have devastating effects on the company's laptop business.In a statement , Huawei said, 'Restricting Huawei from doing business in the US will not make the US more secure or stronger; instead, this will only serve to limit the US to inferior yet more expensive alternatives, leaving the US lagging behind in 5G deployment.' Huawei has reportedly been preparing for such a ban and stockpiled enough chips and components to continue operating for another three months,.
Acer Update Decrypter Executive Orders
It's uncertain what will happen to Huawei laptops once the company faces supply shortages.Huawei and MateBook 14 in February but didn't announce U.S. Pricing and availability.
The company told it 'can't comment at this time' when asked about the future of its laptops.Eyes are now turning to Microsoft to see whether the software giant will follow Google and block Huawei laptops from installing Windows 10 updates. Microsoft told it has 'nothing to share' on the matter, leaving the door open for such a ban. Without Windows 10 updates, Huawei laptop would miss out on new features and potentially remain susceptible to security vulnerabilities. Linux could be a possible safe haven for the company should Microsoft revoke Windows 10 access.The latest actions against Huawei come after the U.S. Announced a on more than $200 billion worth of Chinese exports, which threatens to raise prices on goods that were previously taxed at 10%.The problems Huawei faces continue to compound with no end in sight. You can still buy the and on Amazon.com. However, if you've been eyeing these laptops, you may want to wait until the dust settles before making a purchase. Phillip Tracy,Phillip Tracy is a senior writer at Tom's Guide and Laptop Mag, where he reviews laptops and covers the latest industry news.
After graduating with a journalism degree from the University of Texas at Austin, Phillip became a tech reporter at the Daily Dot. There, he wrote reviews for a range of gadgets and covered everything from social media trends to cybersecurity. Prior to that, he wrote for RCR Wireless News and NewBay Media. When he's not tinkering with devices, you can find Phillip playing video games, reading, listening to indie music or watching soccer.Phillip Tracy, You'd Also Like.
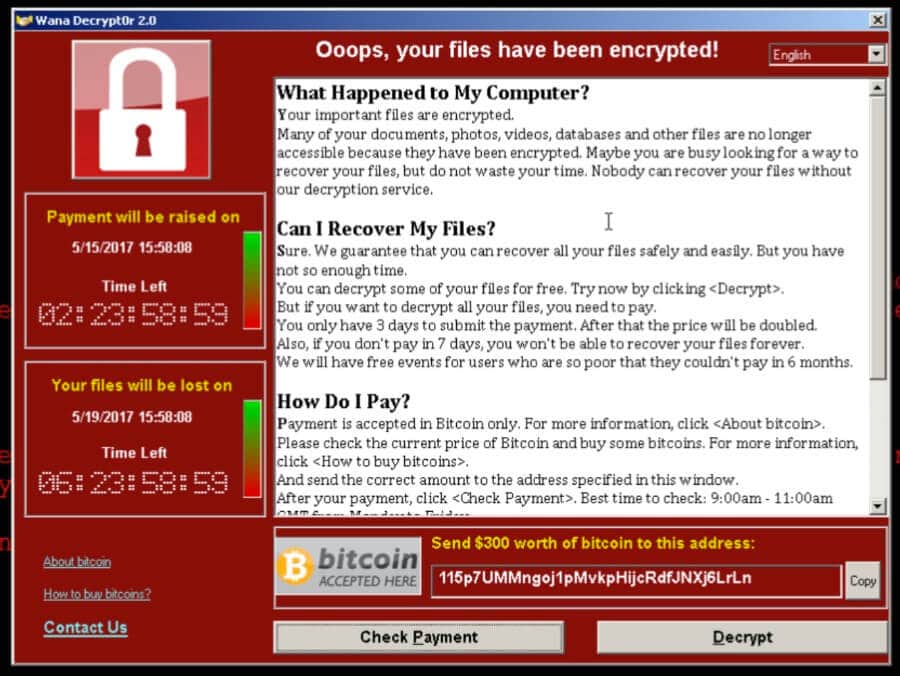
Ransomware is an unfortunate reality for many organizations. Is yours prepared to respond to a ransomware attack or—even better—prevent one from happening?If your business’s files are suddenly encrypted, your operations are halted and your information is at risk, what should you do? What should you know? And what can you learn that would prevent it from happening again?Unfortunately, those questions hit a little too close to home for many organizations of all sizes and structures, and statistics indicate that ransomware isn’t going anywhere for the near future.
According to, ransomware continues to be one of the fastest growing types of cyber-crime, increasing by 350% in 2018, with a business experiencing a ransomware attack every 14 seconds. Enterprise Business saw the biggest increase in ransomware in 2018 according to, and a ransomware published by the Department of Health and Human Services references a U.S. Government interagency alert concerning the ongoing threat of ransomware attacks, which exceeded four thousand per day beginning in 2016.Although the current attack rate is reportedly leveling, ransomware remains a great risk to public and private sectors alike. As one of the top cyber threats, it is important to be aware of what ransomware is and how to defend your organization from attacks. What is Ransomware?According to the“Ransomware is a type of malware that infects computer systems, restricting users’ access to the infected systems. Ransomware variants have been observed for several years and often attempt to extort money from victims by displaying an on-screen alert.
Typically, these alerts state that the user’s systems have been locked or that the user’s files have been encrypted. Users are told that unless a ransom is paid, access will not be restored.
The ransom demanded from individuals varies greatly but is frequently $200–$400 dollars and must be paid in virtual currency, such as Bitcoin.”Ransomware is often spread through phishing emails that contain malicious attachments or through drive-by downloading. Drive-by downloading occurs when a user unknowingly visits an infected website, and then malware is downloaded and installed without the user’s knowledge.Crypto ransomware, a malware variant that encrypts files, is spread through similar methods and has also been spread through social media, such as Web-based instant messaging applications. Additionally, newer methods of ransomware infection have been observed.
For example, vulnerable Web servers have been exploited as an entry point to gain access to an organization’s network.”Some variants of ransomware encrypt the files on the infected device, as well as the contents of shared or networked drives. Ransomware Red Flags to Look fornoted that ransomware is so common that it is found in 39% of cases in which malware was identified, so it’s important to be able to recognize the potential signs of ransomware. When infected, ransomware often displays intimidating messages similar to those below:. “Your computer was used to visit websites with illegal content. To unlock your computer”. “All files on your computer have been encrypted.
You must pay this ransom within 72 hours to regain access to your data.”. “What happened to your files? All of your files were protected by a strong encryption with RSA-2048.
Decrypting your files is only possible with a private key and decrypt program, which is on our secret server. What do I do? So, there are two options: wait for a miracle and get your price doubled, or start obtaining BITCOIN NOW! And restore your data the easy way.”No business or industry is immune from a ransomware attack, but the health industry is being increasingly targeted. The Department of Health and Human Services (HHS) recently spearheaded a joint government-industry cybersecurity Task Group charged with identifying practical approaches to mitigate cyber threats. The group recently published, affectionately referred to as “hiccup,” which identifies email phishing and ransomware attacks as two of the biggest threats against the healthcare industry and our critical infrastructure. If your organization is operating in the healthcare area, it’s even more important to be aware of the red flags of ransomware; your company may be more likely to see them just by operating in your industry.
The Consequences of a Ransomware AttackRansomware is a lucrative business. The amount of data and type of entity compromised will influence the value of the ransom demanded, but on average. In addition to the ransom many businesses end up paying, damages in ransomware attacks are projected to be.Businesses may experience financial losses as a result of a ransomware attack in order to restore files and systems, but there are also many other consequences that come with ransomware attacks. Systems infected with ransomware are also often infected with other malware as well, which can further the damage done to your company’s systems even more. Consequences may also include the temporary or permanent loss of sensitive or proprietary information, a disruption to your company’s regular operations and damage to your company’s reputation. The extent of the damage can vary greatly from business to business depending on the attack.
How to Protect your Company against a Ransomware AttackAny organization without a ransomware protection strategy is taking a big risk. The best way to protect your company against a ransomware attack is to establish sound policies, implement effective security software and to educate your workforce about best practice.First, you must establish a reliable backup system for your data.
You should also consider historical backup archive retention with sufficient depth; this can permit recovery when an attack is slow to develop and when infected files are backed up. It is similarly important to store backup files apart from the production environment, so that backups are not encrypted along with other data. It’s also important to remember that current-day malicious code consists mostly of fileless varieties, which are not adequately defended by traditional anti-virus and endpoint security methods. To better defend against these cybersecurity threats, your organization should reassess its endpoint security. An effective approach calls for new Advanced Endpoint Security functionality, which establishes an operational baseline and automatically halts untrusted actions within the network.
(You can reference for comparisons.)It is also important to train and educate your company’s employees about ransomware, cybersecurity dangers and what they should know and can do to prevent an attack on their own part. An educated workforce is the organization’s first line of defense against social engineering and phishing attacks.
Internal controls are important too. In 2018, and 17% of cyber breaches could be traced back to an employee error. Security awareness training for employees should include email security testing to ensure that users can recognize threatening email messages, and it should educate your team members about organizational policies and procedures, including password controls and system security.
Weaknesses in access controls and password security, as well as unpatched software vulnerabilities, have been identified as entry points for many ransomware variants. How to Respond to a Ransomware AttackMost often, a ransomware attack is first identified after a user is unable to open a file and reports an error containing a ransom message, such as those examples provided above. The first step when an attack is detected is to disconnect infected computers from the network and Internet. Encryption processes take time, so this will mitigate the extent of the damage.Before responding to any ransom demand, consult your cyber liability insurance company and your legal counsel for advice.
Remember that individuals or organizations are discouraged from paying the ransom, as this does not guarantee files will be released; it only guarantees that the malicious actors receive the victim’s money and, in some cases, banking information. In addition, decrypting files does not mean the malware infection itself has been removed, so it is helpful to have the to guide your recovery process. Always report instances of fraud to the FBI at the.Malware Hunter Team operates a free, called ID Ransomware, which is dedicated to defending against ransomware. If the ransomware can be identified, ID Ransomware will give the victim a distinct status on whether the ransomware variant is known to be decryptable or not, and it will provide a link to a credible source for more information. The FBI will also have this type of information. More Ransomware ResourcesHopefully, by implementing good security habits, you will be successful in avoiding a costly ransomware incident.This article was originally written by Jeff Bohman and published by Warren Averett on November 28, 2017.
It has been most recently updated with new statistics and insight on April 10, 2019. Warren Averett is a top 35 accounting firm providing audit, tax, accounting and consulting services to companies across the Southeast. Our Firm has expertise in industries including manufacturing, construction, real estate, financial services, healthcare, government, education, and retail.
We serve clients from office locations including Birmingham (AL), Atlanta (GA), Tampa (FL), Montgomery (AL), Huntsville (AL), Pensacola (FL), Fort Walton (FL), Destin (FL), Panama City (FL), Cullman (AL), Anniston (AL), Mobile (AL), and Foley (AL).© 2019 Warren Averett CPAs & Advisors. All rights reserved.